AI security
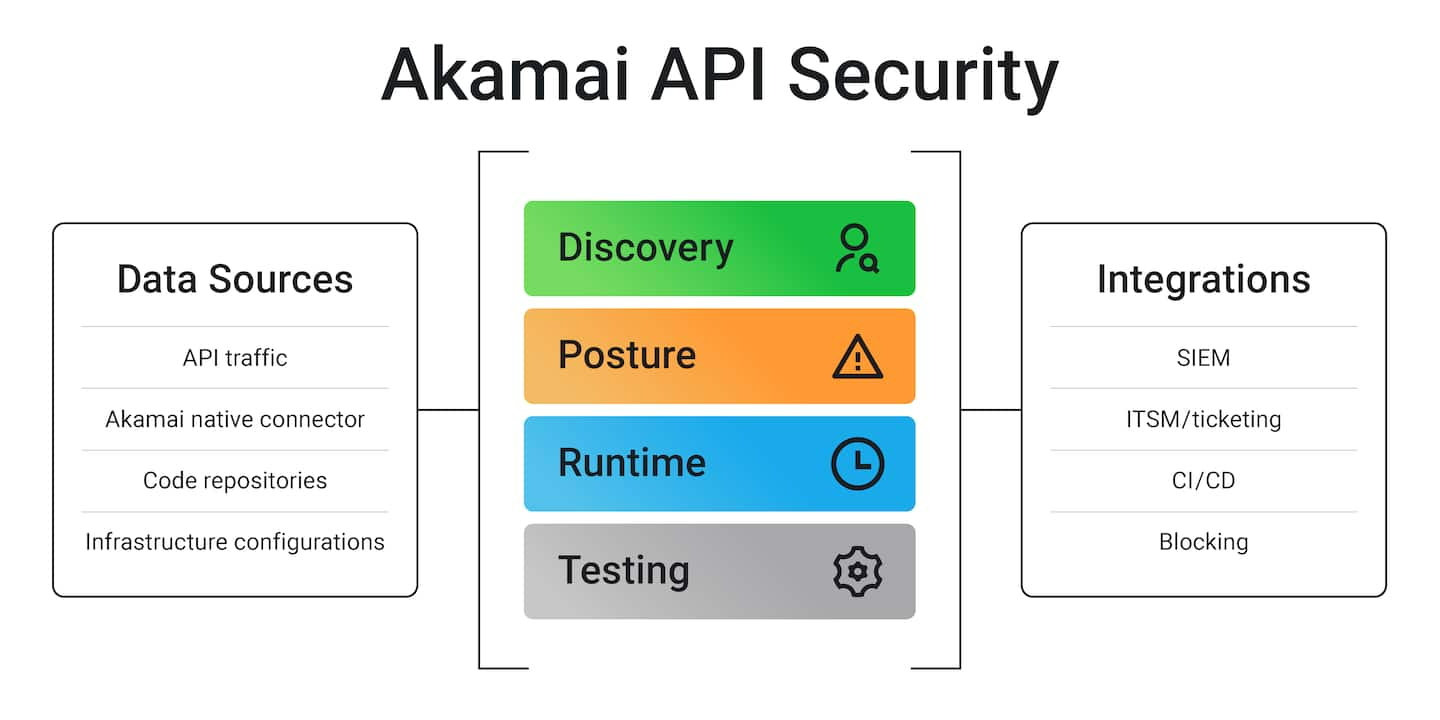
AI security for APIs delivers proactive defense against sophisticated threats targeting both traditional and AI-powered applications. By automatically discovering and classifying APIs that interact with GenAI models, LLMs, and AI services — including shadow or unmanaged endpoints — security teams can gain real-time visibility, enforce governance, and reduce compliance risks.
Test APIs before putting them into production
API testing is critical for your API security strategy because it helps organizations “shift left” — detecting and fixing vulnerabilities such as business logic abuse earlier in the software development lifecycle (SDLC), before APIs reach production.
With API testing, you can automatically run 150+ dynamic tests that simulate malicious traffic, including against the OWASP Top 10 API Security Risks. Schedule tests to run automatically at desired intervals at any stage of development.
Get an enterprise-wide inventory of your APIs
Maintaining a comprehensive and continuously updated inventory of all APIs across your organization is crucial for an effective API security strategy. On-demand or daily discovery is insufficient due to the severity of risks associated with API attacks. Moreover, visualizing actual API behavior (API calls) is necessary to enable key team members from security, development, and operations to understand how APIs are being used or misused. This facilitates communication and investigation across your organization’s teams.
API Security offers automated and continuous discovery of APIs across various technologies and infrastructure. It also identifies newly deployed APIs and compares their properties with existing documentation. API Security detects often-missed shadow APIs and known API vulnerabilities, such as those outlined in the OWASP Top 10 API Security Risks.
API discovery is an ongoing process, and our continuous monitoring finds new APIs and changes to existing ones around the clock. Security teams gain unparalleled visibility and are the first to know when developers deploy a new API or service.
Understand your API risk posture
APIs fuel every digital product and service that an enterprise rolls out. So it’s no surprise APIs are growing in scope and scale. But this proliferation leads to an API sprawl that is reshaping your attack surface.
Today’s attackers look for API vulnerabilities — including software bugs or configuration errors — that they can exploit to:
- Gain access to sensitive application functionality
- Find, compromise, and/or steal sensitive data
- Misuse the API in malicious ways
The OWASP Top 10 API Security Risks provide a helpful summary of some of the most commonly exploited API vulnerabilities and threats that organizations should try to identify and address.
With API security, you can prevent vulnerable and misconfigured APIs from exposing your enterprise to API attacks by promptly notifying security, developer, and API teams of potential risks, configuration errors, and vulnerabilities. You can also easily determine if a partner has set up your API incorrectly or if there are vulnerabilities in the code.
Contextual and conditional alerts work seamlessly within your existing workflows, such as by automatically creating a Jira ticket, enabling you to swiftly resolve any issues.
Monitor API abuse
APIs are designed to be used programmatically, which makes differentiating legitimate usage from attacks and abuse extremely challenging.
While API attack methods vary, some of the most common approaches include:
- Business logic abuse. Business logic attacks exploit application design or implementation flaws to prompt unexpected and unsanctioned behavior benefiting the attackers.
- Unauthorized data access. This common attack method exploits broken authentication and authorization mechanisms to access restricted data.
- Account takeover. Account takeover relies on credential theft or cross-site scripting attacks to exploit APIs by pretending to be a legitimate user.
- Data scraping. Malicious actors may aggressively query publicly available resources to perform the wholesale capture of large, valuable datasets.
- Business denial of service (DoS). Unrestricted API calls can cause “erosion of service” or a complete denial of service at the application layer.
Detecting and preventing these and other potential API security risks necessitates using advanced controls available in dedicated API security solutions as part of your broader application security strategy.














 Loading ...
Loading ...