RED TEAMING
VietSunshine experts will conduct comprehensive penetration testing across various contexts and scopes, simulating attack chains and escalating through penetration across each system.
What is Red Teaming?
Red Teaming is a term originating from the military domain, simulating comprehensive cyber attacks. It's a way to test your network defense capabilities against adversaries. Red Teaming enables your defensive team to practice so they can fine-tune their response capabilities in a controlled environment. Additionally, Red Teaming can uncover security vulnerabilities. Unlike conventional penetration testing, it targets your organization without constraints.

Benefits of Red Teaming
Identifying vulnerabilities: Red Teaming helps identify both technical and non-technical vulnerabilities in your system that might be overlooked by less comprehensive assessments.
Testing incident response: Red Teaming allows organizations to test their incident response procedures. This can help uncover issues with incident response plans, such as slow detection times or poor communication between teams.
Providing realistic threat scenarios: This can provide organizations with a more realistic understanding of their security posture.

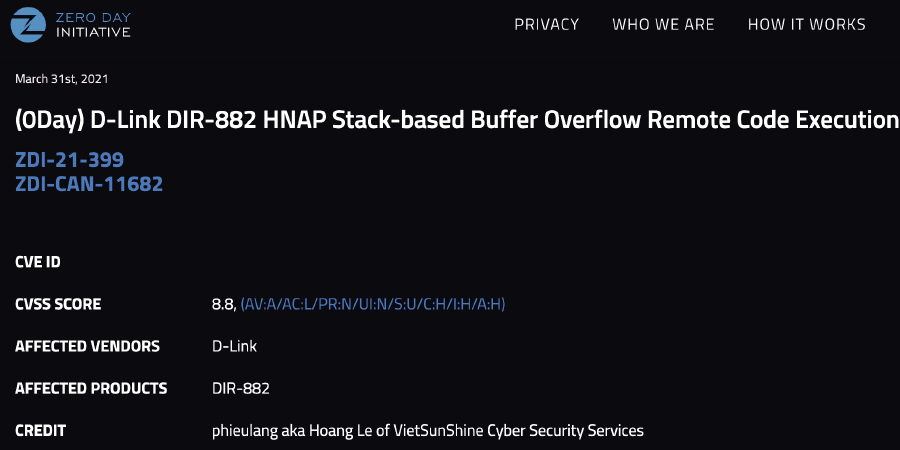
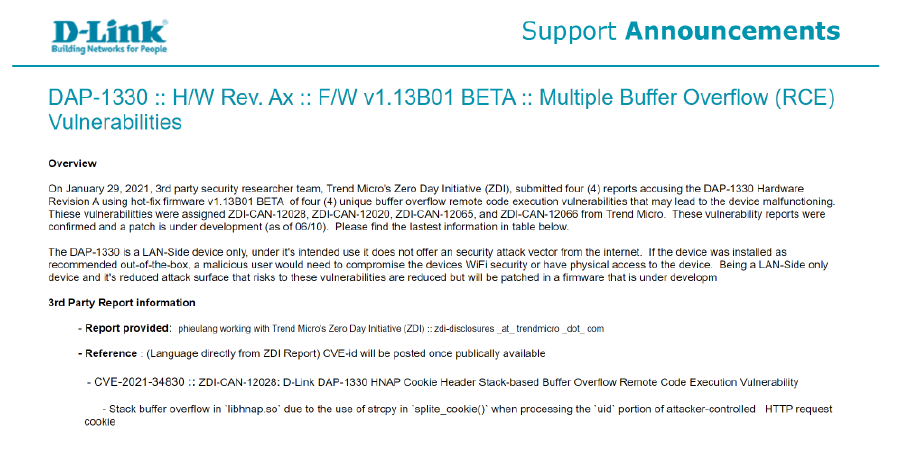
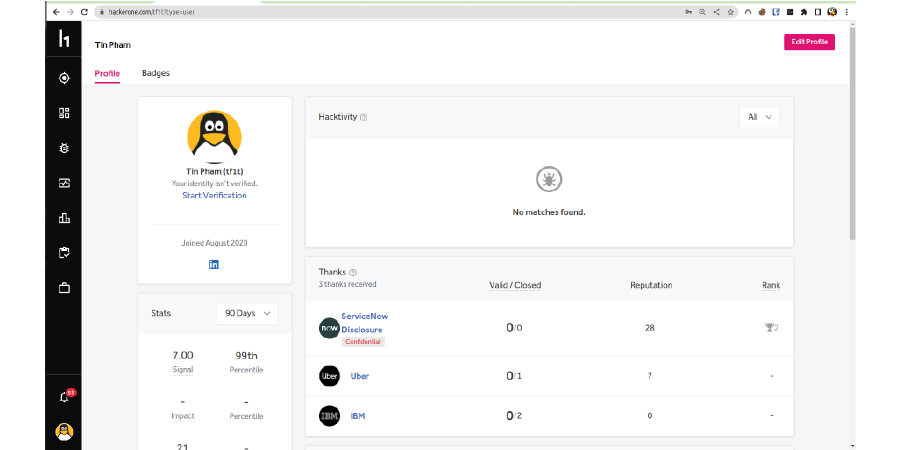
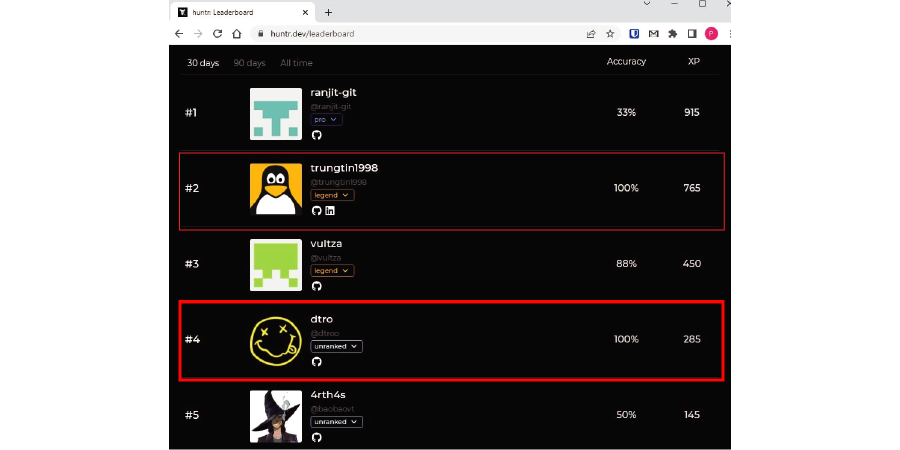
Awards and achievements
MODELS AND TECHNIQUES
- Objective: Simulate real-world cybercriminal attacks, utilizing advanced penetration techniques, chaining vulnerabilities, bypassing defense systems, to assess intrusion detection capabilities and data theft.
- Scope: Typically defines an open scope, such as selecting areas outside the Internet, or internal system areas, to conduct intrusion.
- Method: Employ flexible intrusion tactics and techniques based on the organization's current status, each phase of intrusion, without fixating on scenarios.
- Report: Provide an overall picture of potential security vulnerabilities leading to system compromise, assess the active detection and response capabilities of defense systems against advanced intrusion forms.
Some common contexts:
- External Attack: Attacks originating from the Internet, exploiting online service channels accessible to anyone.
- Internal Attack: Simulating scenarios where internal systems are breached, and a hacker gains control over an employee's computer.
- Wireless Network Attack: Attacks targeting wireless networks, determining whether access through wireless networks can breach other systems.
- Data Exfiltration Attack: Attacks aimed at extracting data.
ATT&CK Matrix for Enterprise
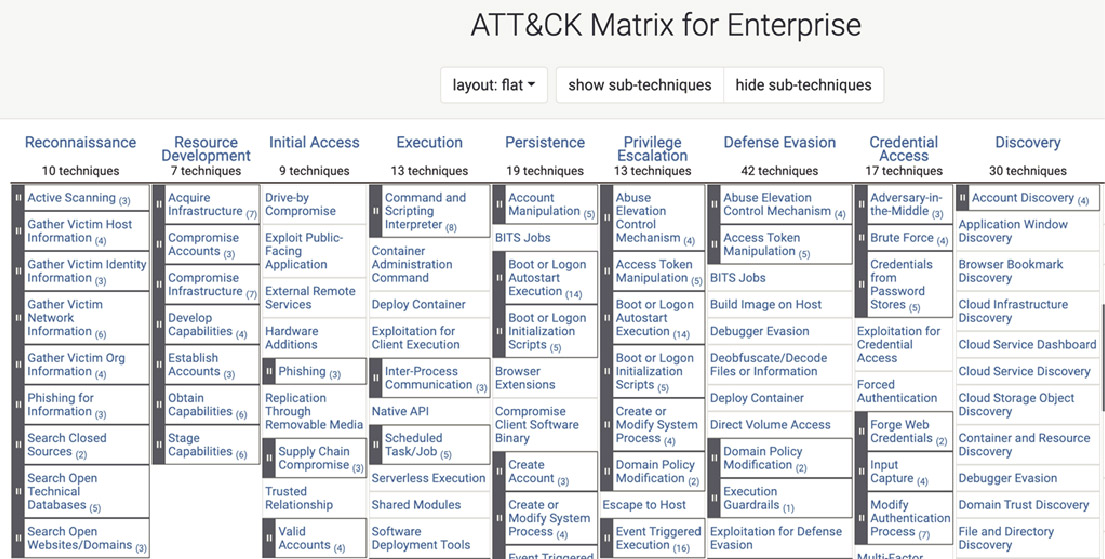
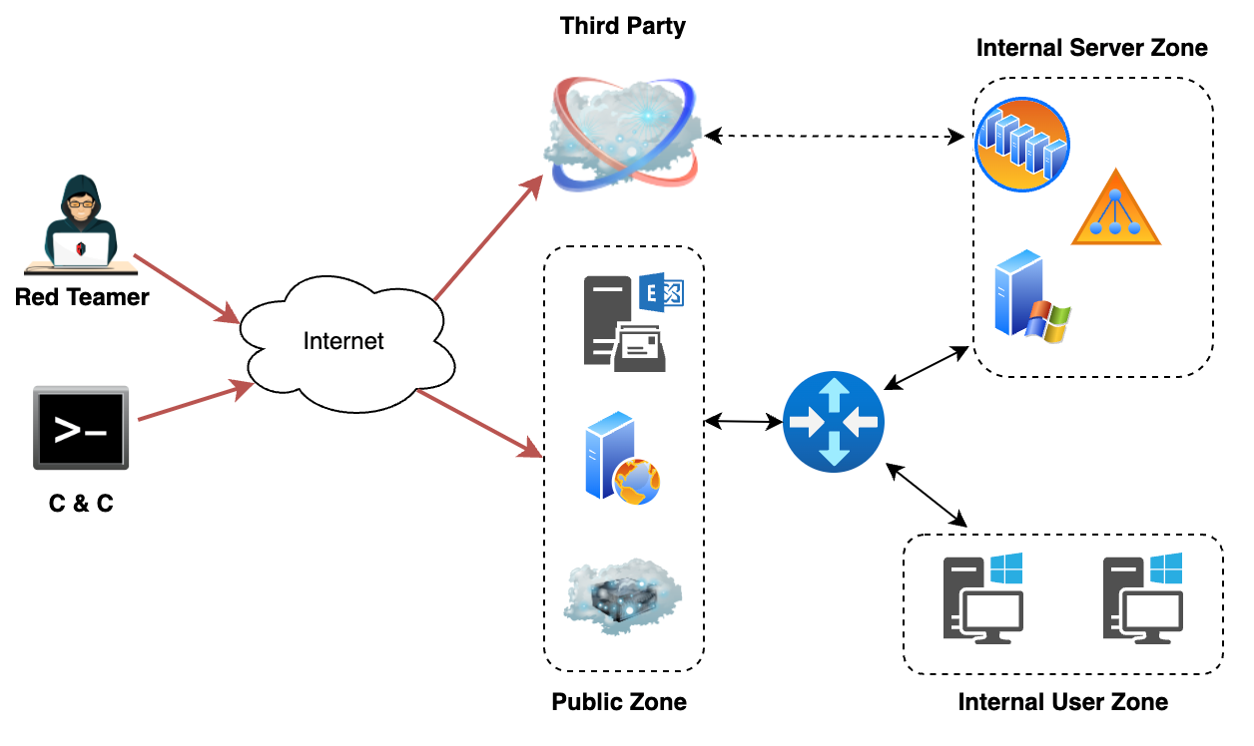
Illustration of attack flow

Leave contact
and we can advise you
We are happy to share advice and guide you with ideas about the service you need most










 Loading ...
Loading ...